Our Technology
The network communications industry has many technologies that support and improve
communication over various networks. Our technology brings security with numerous network
optimizations into the mix.
The technology is a device driver framework that implements a concept of man-in-the-middle
(MITM) TCP/IP stack. It is a TCP/IP networking stack built from the ground up specifically
for the purposes of security and optimizations. It allows parties of network conversations
to communicate transparently without noticing that optimizations and security checks are
taking place. The framework supports many currently popular network protocols and performs
programmable operations within the heart of the operating system - within device drivers.
Modern security frameworks implement security analysis within the application space by
requiring applications either to link or to load modules that perform certain functions.
In contrast, our technology operates transparently within the operating system and does
not require any modifications to legacy software. It can be installed and updated
independently of applications. The overhead of other security frameworks due to operations
within the application space could be substantial. Therefore, the advantages of using our
technology are easy to notice:
- Faster performance, since device drivers operate at higher priorities than
application space programs.
- Better performance due to memory optimizations. There are no unnecessary transfers
of memory blocks back and forth between the OS and applications.
- Early detection and filtering out of suspicious activities and their removal from
network conversations.
- There are no additional requirements for applications to use specific technologies
or to link to specific libraries.
- Easy to upgrade and virtually no compatibility conflicts.
Other security frameworks
|
Verigio framework
|
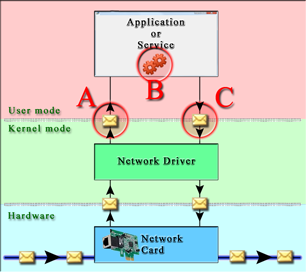 |
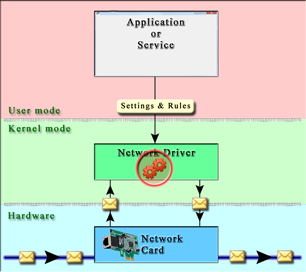 |
In the above diagram, red circles with letters indicate inefficiencies that other
frameworks are suffering from. Those inefficiencies waste CPU time and reduce
performance of the whole computer, not only its networking subsystem. Their impact on
performance can be summarized as follows:
(A) and
(C)
Kernel-mode to user-mode transition.
- [CPU, MEMORY] Allocation and copying of memory during data transfer between
kernel-mode and user-mode for every packet.
- [CPU] Serialization of data transfer. This voids the benefits of multi-core
processors.
- [CPU] Overhead of switching from kernel-mode to user-mode.
(B) User-mode traffic processing.
- [CPU] User-mode traffic processing is executed on user-mode threads that compete
for CPU with other applications.
- [CPU,MEMORY] Possibility of memory being paged out into a page file.
- [CPU,MEMORY] Queuing of data caused by processing slower than incoming data from
kernel-mode.
Just like other security frameworks, our framework can work fully within the application
space as well. But many more benefits come from its use within device drivers. That is
something that other frameworks cannot easily match. With the precise implementation of
optimizations of common processing bottlenecks, our framework allows you to get the most
out of the existing hardware and VMs.