Geo Firewall configuration for 3CX PBX with NGINX
This article applies to the following products:
Problem Description
After installing and successfully starting Geo Firewall, you may observe the following
symptoms:
- Unable to reach the 3CX management console from the internet.
- Unable to reach other running services on TCP port 443 (HTTPS).
- When running a test on the ports, you get the following message: "testing port
9000... full cone test failed"
- However, the management console can be accessed locally without any problems.
Analysis of the Issue
By default, Geo Firewall blocks all incoming and
outgoing communication with the countries and territories selected for blocking. The
3CX management console and some other 3CX services
require certain TCP and UDP ports to be always
accessible (open) for incoming traffic. Please refer to the 3CX
documentation for information on which ports need to be open
(https://www.3cx.com/docs/ports/)
Solution
The relevant TCP and UDP ports should be opened for
incoming traffic in both Windows Firewall and Geo Firewall.
In Geo Firewall, the ports can be opened on the Port Exceptions
tab of the main window.
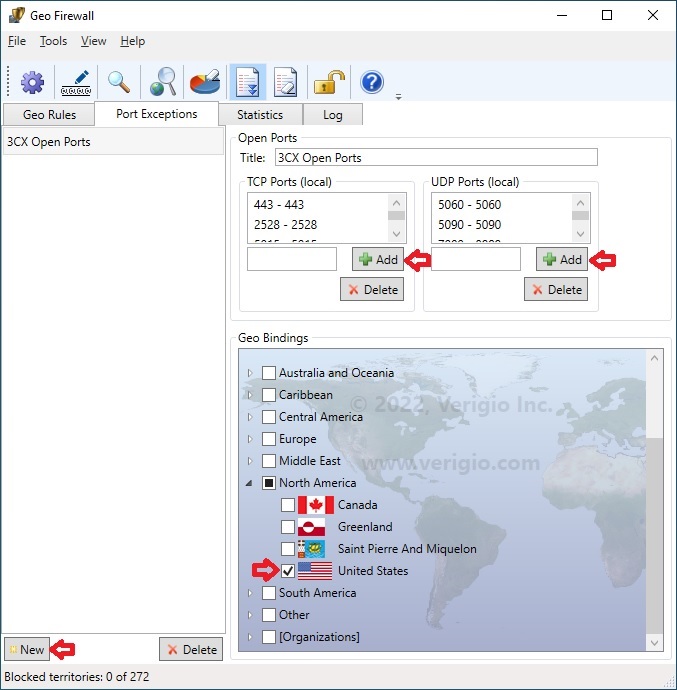
- Navigate to the Port Exceptions tab.
- Add a new exception rule by clicking the New button at the
bottom-left.
- Give the rule a name in the Title field.
- Using the 3CX documentation on open ports, add the necessary
TCP and UDP ports to their respective lists.
- Assign a geographical binding. This is the geographical scope where this exception
rule will be active.
Example:
3CX ports are open for access from the United States.
This is the content of the 3cx.xvgf file that can be imported into Geo Firewall
for the example above.
<?xml version="1.0" encoding="utf-8"?>
<GeoFirewallRules xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" version="1">
<portexception name="3CX Open Ports">
<geocodebinding>US</geocodebinding>
<TCPPortRange min="443" max="443" />
<TCPPortRange min="2528" max="2528" />
<TCPPortRange min="5015" max="5015" />
<TCPPortRange min="5060" max="5060" />
<TCPPortRange min="5061" max="5061" />
<TCPPortRange min="5090" max="5090" />
<UDPPortRange min="5060" max="5060" />
<UDPPortRange min="5090" max="5090" />
<UDPPortRange min="7000" max="8999" />
<UDPPortRange min="9000" max="10999" />
</portexception>
</GeoFirewallRules>
Last updated: Oct 16, 2025.